KYC Passport
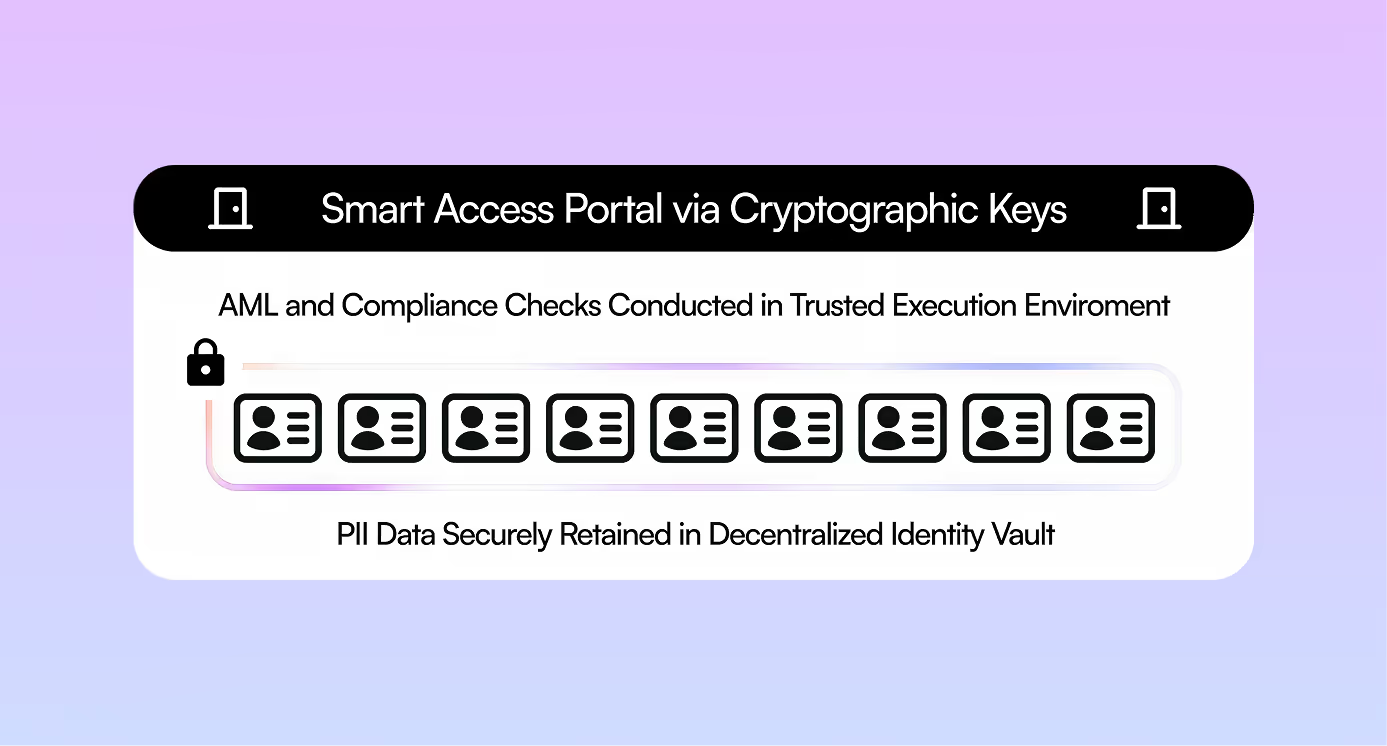
Data from Zyphe’s decentralized personal identity vaults can be easily and securely re-shared with authorized parties, which helps to avoid friction and PII retention risks.
Data from Zyphe’s decentralized personal identity vaults can be easily and securely re-shared with authorized parties, which helps to avoid friction and PII retention risks.




































Countries around the world covered by Zyphe for compliant KYC processing and AML monitoring
More resistant to data breaches vs. traditional data access & storage
Lower expenses for compliance processes at typical companies
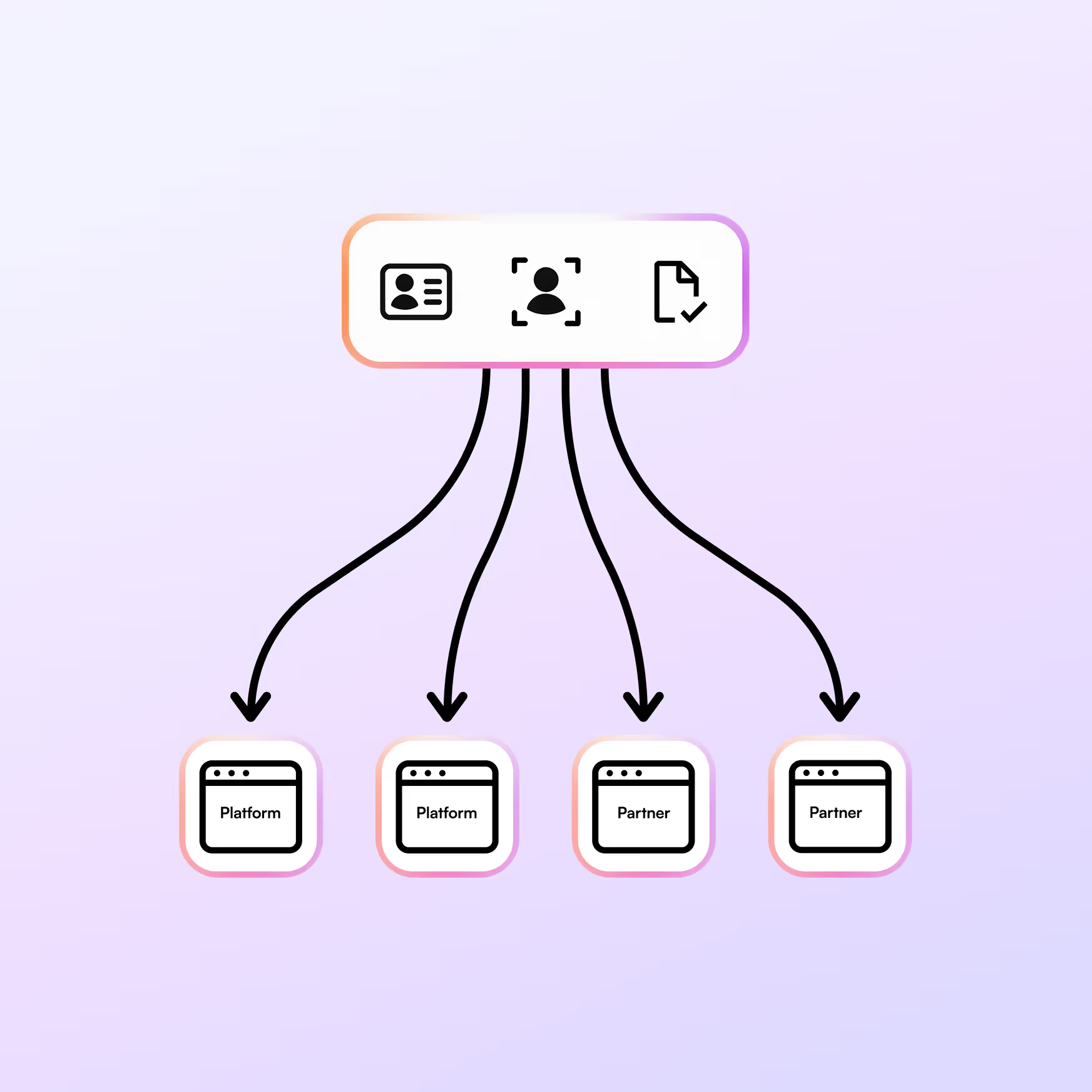
Users grant smart authorization through one click for any portion of their KYC data and biometrics to be easily shared with multiple partners or platforms who need KYC checks.
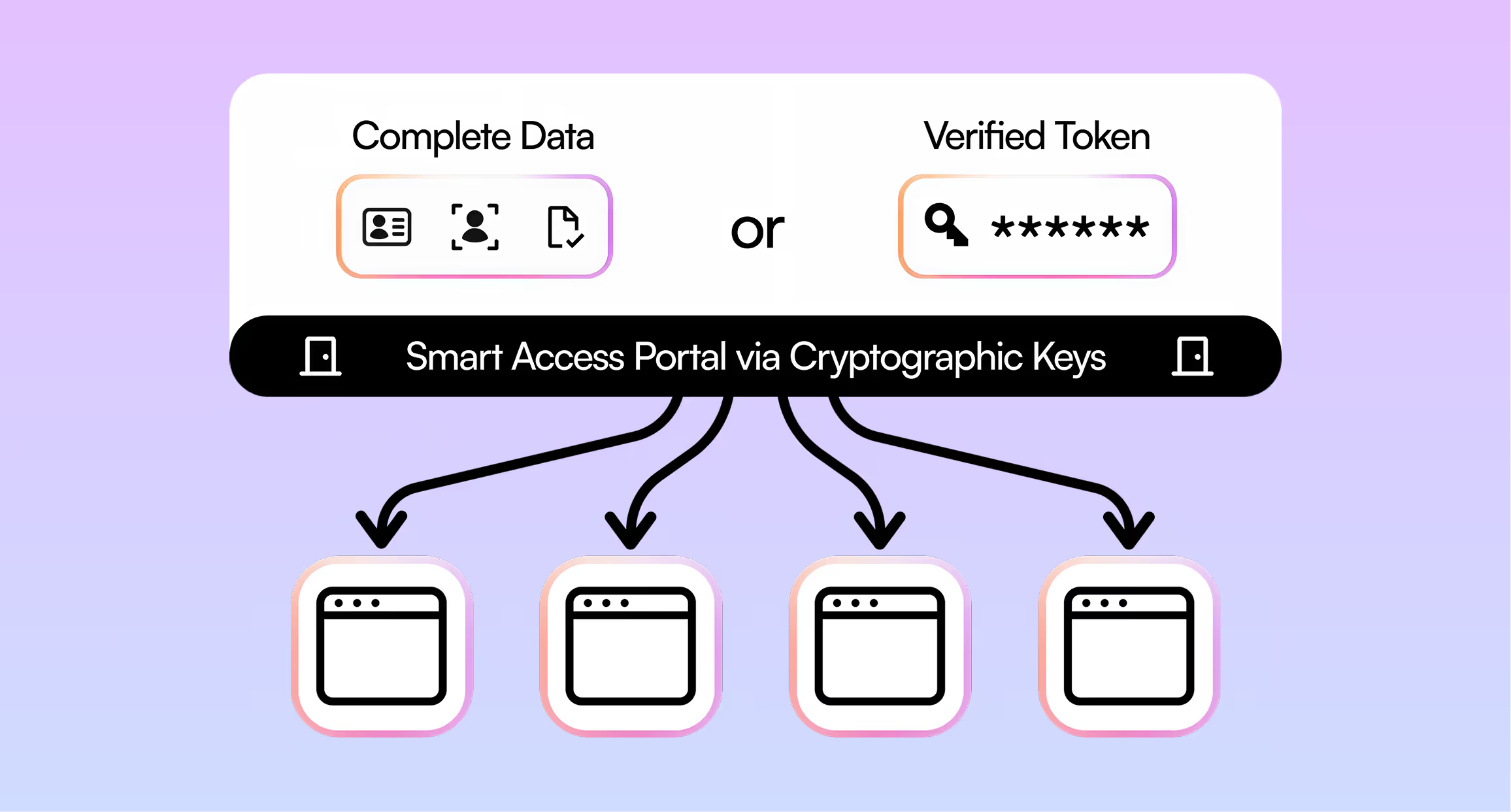
Users only undergo a single KYC onboarding experience and do not need to re-submit documents or biometrics, even if partners prefer to run different checks on the same documents.
With Zyphe’s decentralized personal identity vaults secured by individual cryptographic keys, avoid having to retain additional copies of PII data and data breach risks from partners, platforms, and intermediaries.